Инструмент PingCastle позволяет провести проверку безопасности AD. После прохождения более 100000 тестов безопасности формируется удобный отчет. Французы молодцы. Пользоваться не просто, а очень просто.
Установка не требуется, изменение данных не производится, данные не отправляются в облако, вы получаете HTML отчёт. Возможны ложные срабатывания, потому как PingCastle учитывает потенциальные риски в том числе. Есть поддержка командной строки.
PingCastle можно скачать бесплатно. Код доступен по лицензии Non-Profit Open Software License ("Non-Profit OSL") 3.0. Бесплатная версия позволяет выполнить:
- Audit Program
- Health Check Report
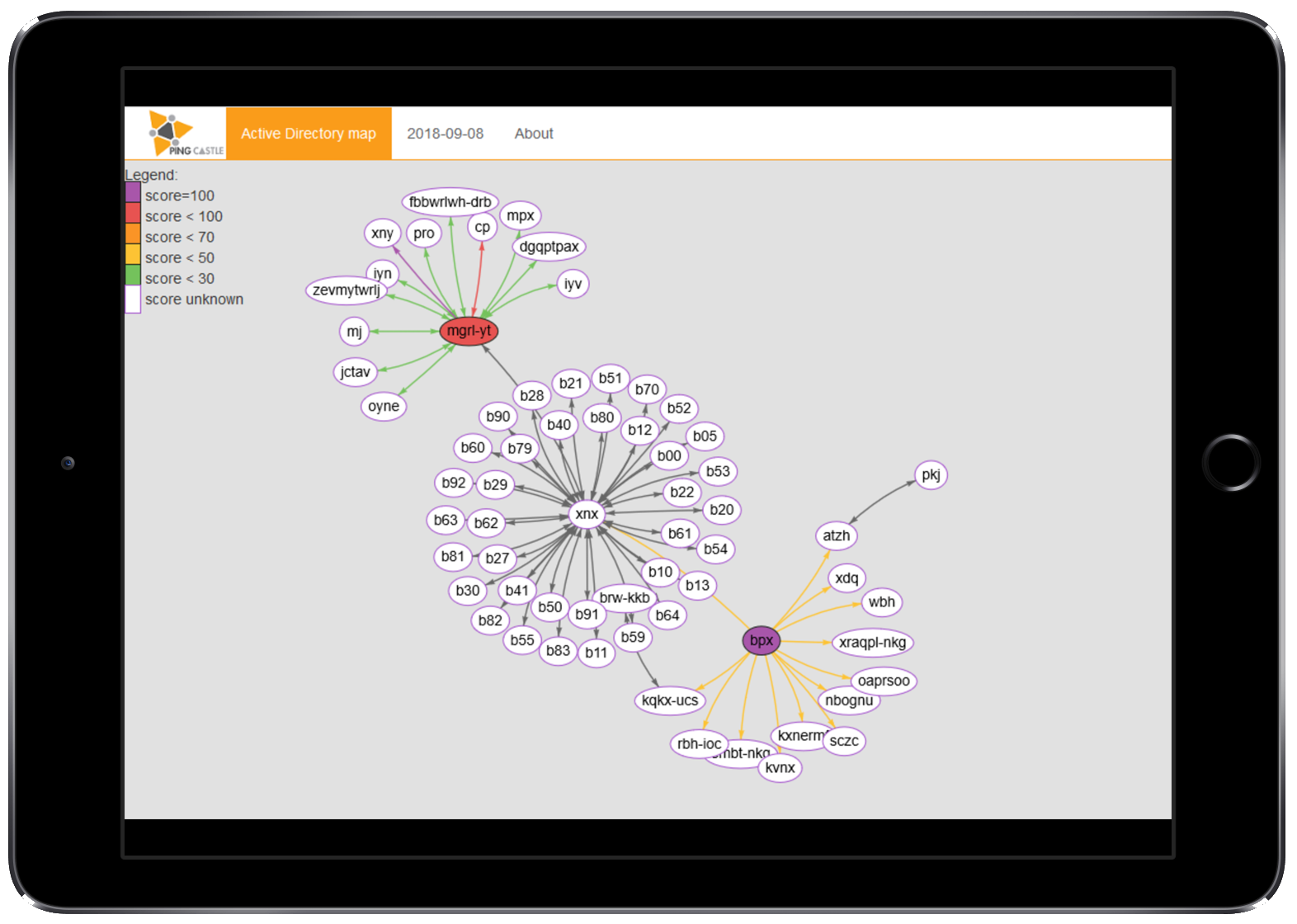
- Map
Установка PingCastle
Установки, как таковой не требуется.
https://www.pingcastle.com/download
Скачиваем последний релиз. Доступна версия 3.1.0.0. Распаковываем архив.
Запуск PingCastle
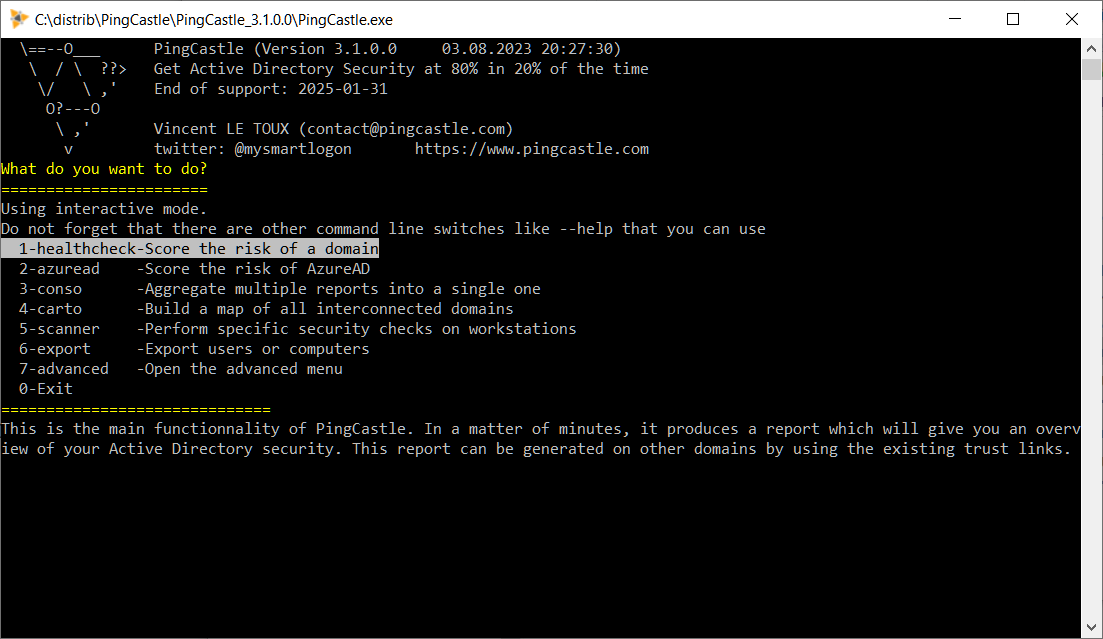
Запускаем PingCastle.exe. Делать это можно на любом компьютере домена, запуск с контроллера домена не требуется.
Видим консольное меню, стрелками выбираем нужный пункт.
- healthcheck — основной отчёт о безопасности AD
- azeread — отчёт о безопасности AD в облаке Azure
- conso — консолидация всех отчётов в один, генерация карты
- carto — построение карты доменов
- scanner — сканирование ПК
- export — экспорт списка пользователей или компьютеров
- advanced — выбор опций запуска PingCastle
Следуем дальнейшим инструкциям и в конечном итоге получаем HTML файл с отчётом.
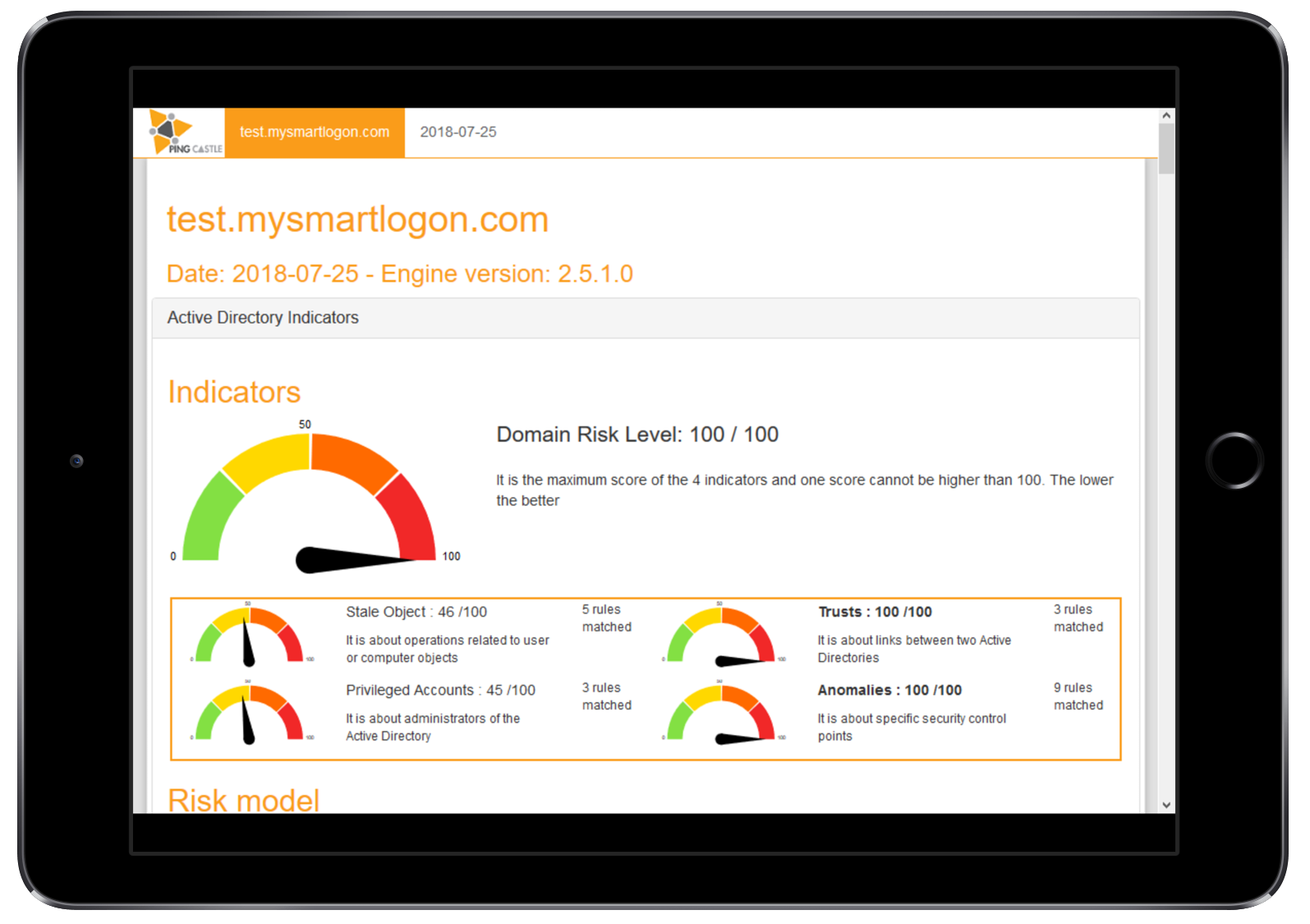
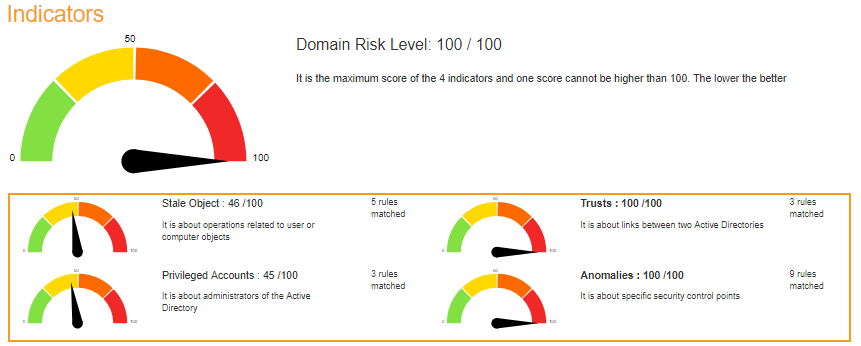
Отчёт подробный, в верхней части выводится общая оценка безопасности.
Общая оценка складывается из 4 индикаторов:
- Privileged accounts — про админов
- Trusts — связь между доменами
- Stale objects — про AD
- Security anomalies — всё остальное
Запуск в командной строке:
PingCastle.exe --healthcheck --server mydomain.com
-
PingCastle.exe --help
switch: --help : display this message --interactive : force the interactive mode --log : generate a log file --log-console : add log to the console --log-samba <option>: enable samba login (example: 10) --api-endpoint <> : to upload report via api call eg: http://server --api-key <key> : and using the api key as registered Common options when connecting to the AD --server <server> : use this server (default: current domain controller) the special value * or *.forest do the healthcheck for all domains --port <port> : the port to use for ADWS or LDAP (default: 9389 or 389) --user <user> : use this user (default: integrated authentication) --password <pass> : use this password (default: asked on a secure prompt) --protocol <proto> : selection the protocol to use among LDAP or ADWS (fastest) : ADWSThenLDAP (default), ADWSOnly, LDAPOnly, LDAPThenADWS --pagesize <size> : change the default LDAP page size - default is 500 --quota <num> : Number of LDAP items per second that will be processed - default unlimited --carto : perform a quick cartography with domains surrounding --healthcheck : perform the healthcheck (step1) --explore-trust : on domains of a forest, after the healthcheck, do the hc on all trusted domains except domains of the forest and forest trusts --explore-forest-trust : on root domain of a forest, after the healthcheck, do the hc on all forest trusts discovered --explore-trust and --explore-forest-trust can be run together --explore-exception <domains> : comma separated values of domains that will not be explored automatically --datefile : insert the date into the report filename --encrypt : use an RSA key stored in the .config file to crypt the content of the xml report --level <level> : specify the amount of data found in the xml file : level: Full, Normal, Light --no-enum-limit : remove the max 100 users limitation in html report --reachable : add reachable domains to the list of discovered domains --sendXmlTo <emails>: send xml reports to a mailbox (comma separated email) --sendHtmlTo <emails>: send html reports to a mailbox --sendAllTo <emails>: send html reports to a mailbox --notifyMail <emails>: add email notification when the mail is received --smtplogin <user>: allow smtp credentials ... --smtppass <pass> : ... to be entered on the command line --smtptls : enable TLS/SSL in SMTP if used on other port than 465 and 587 --skip-null-session: do not test for null session --webdirectory <dir>: upload the xml report to a webdav server --webuser <user> : optional user and password --webpassword <password> --max-depth : maximum number of relation to explore (default:30) --max-nodes : maximum number of node to include (default:1000) --node <node> : create a report based on a object : example: "cn=name" or "name" --nodes <file> : create x report based on the nodes listed on a file --I-swear-I-paid-win7-support : meaningless --I-swear-I-paid-win8-support : meaningless --I-swear-I-paid-win2012-support : meaningless --rules : Generate an html containing all the rules used by PingCastle --generate-key : generate and display a new RSA key for encryption --hc-conso : consolidate multiple healthcheck xml reports (step2) --center-on <domain> : center the simplified graph on this domain default is the domain with the most links --xmls <path> : specify the path containing xml (default: current directory) --filter-date <date>: filter report generated after the date. --regen-report <xml> : regenerate a html report based on a xml report --reload-report <xml> : regenerate a xml report based on a xml report any healthcheck switches (send email, ..) can be reused --level <level> : specify the amount of data found in the xml file : level: Full, Normal, Light (default: Normal) --encrypt : use an RSA key stored in the .config file to crypt the content of the xml report the absence of this switch on an encrypted report will produce a decrypted report --scanner <type> : perform a scan on one of all computers of the domain (using --server) aclcheck Check authorization related to users or groups. Default to everyone, authenticated users and domain users antivirus Check for computers without known antivirus installed. It is used to detect unprotected computers but may also report computers with unknown antivirus. computerversion Get the version of a computer. Can be used to determine if obsolete operating systems are still present. foreignusers Use trusts to enumerate users located in domain denied such as bastion or domains too far away. laps_bitlocker Check on the AD if LAPS and/or BitLocker has been enabled for all computers on the domain. localadmin Enumerate the local administrators of a computer. nullsession Check if null sessions are enabled and provide example(s). nullsession-trust Dump the trusts of a domain via null session if possible oxidbindings List all IP of the computer via the Oxid Resolver (part of DCOM). No authentication. Used to find other networks such as the one used for administration. remote Check if a remote desktop solution is installed on the computer. share List all shares published on a computer and determine if the share can be accessed by anyone smb Scan a computer and determine the smb version available. Also if SMB signing is active. smb3querynetwork List all IP of the computer and the interface speed using SMB3. Authentication required. Used to find other networks such as the one used for administration. spooler Check if the spooler service is remotely active. The spooler can be abused to get computer tokens when unconstrained delegations are exploited. startup Get the last startup date of a computer. Can be used to determine if latest patches have been applied. zerologon Test for the ZeroLogon vulnerability. Important: the tester must be inside the domain. Trusts cannot be used. options for scanners: --scmode-all : scan all computers (default) --scmode-single : force scanner to check one single computer --scmode-workstation : force scanner to check workstations --scmode-server : force scanner to check servers --scmode-dc : force scanner to check dc --scmode-file <file> : force scanner to use the computer from file --nslimit <number>: Limit the number of users to enumerate (default: unlimited) --foreigndomain <sid> : foreign domain targeted using its FQDN or sids Example of SID: S-1-5-21-4005144719-3948538632-2546531719 --export <type> : perform an export of objects of the domain (using --server) azureguest Export all AzureAD users from an AzureAD guest account changes Export all modifications that occurs in the domain in real time computers Export all computers users Export all users Common options when connecting to AzureAD --tenantid xx: specify the tenant id to use. Requiered for cert auth Authentication --use-prt : use prt to log on Certificate authentication --clientid xxx : specify the client id to which the certificate is associated With private key --thumbprint xxx : specify the thumprint of the certificate configured --private-key xxx : specify the key file to use (PKCS8) With P12 --p12-file xxx : specify the P12 file to use --p12-pass xxx : specify the password to use --upload-all-reports: use the API to upload all reports in the current directory --api-endpoint <> : upload report via api call eg: http://server --api-key <key> : and using the api key as registered Note: do not forget to set --level Full to send all the information available --export-rules : export all rule in a single xml file
Процесс генерации отчёта PingCastle.